Transportation Logistics Are Under Cyber Attack
Are you prepared to meet the threat?
Cyber attackers have set their sights on transportation & logistics companies.
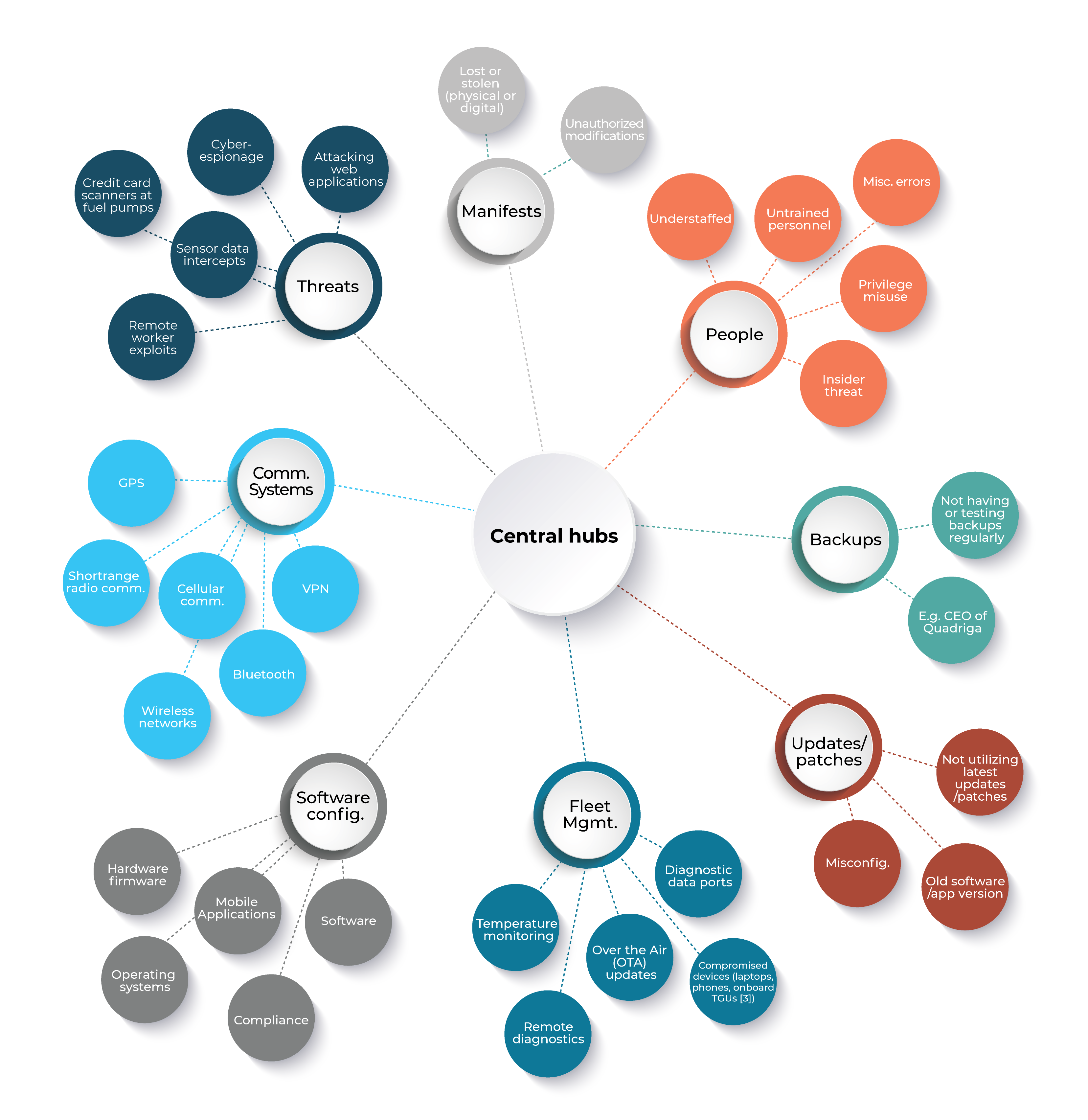
Logistics require central hubs, applications, and control to track shipments, vehicles, assets, etc but suffer an outsized impact if exploited or taken offline by cyber attacks. Systems like fleet management , GPS, manifests, and logistical plans are susceptible to cyberattacks. It’s vital for transportation and logistics companies to review and assess their cybersecurity.
The strained supply chain has increased the likelihood of targets on transportation and logistics companies. These targets have come in a variety of attacks including Insider Attacks, Phishing, Zero-day exploits, account takeovers, data and IP theft, and ransomware. In our experience, we have noticed a trend of attackers re-targeting a previously exploited firm – Once a soft target is identified, they are often targeted multiple times in order to extract additional ransom, data, IP, or to disrupt operations. This has a huge impact financially and reputationally.
There are a variety of ways attackers are targeting organizations in the T&L sector, and the ever-growing number of edge devices means there are more opportunities for exploitation than ever. These devices have introduced a multitude of attack vectors that are being exploited by hackers and cyber attackers. These include everything from web applications, wireless networks, and bluetooth to entry points you may not have considered like diagnostic ports, temperature monitors, and over the air updates. As trucks become increasingly outfitted with smart devices, the opportunity for exploitation continues to grow.
Most Common Cyber Attacks in the Trucking and Logistics Industry

BYOD
Allowing the use of BYoD can lead to data and network integrity issues from malware or jail-broken devices. Lack of data encryption increases the risk of data loss to include PII or proprietary information. Lack of proper configuration of the different device types and settings can, and usually does, lead to compromise.

Unhardened Networks
Unfettered connections between systems allows lateral spread of malware and nefarious actors. Additionally, it allows data of different classifications or sensitivity to be exposed to the least secure components. Security is only as strong as the weakest link of a chain.

Wireless
Connectivity
Wireless risks are expanding at an alarming rate. A few of the risks are “Piggybacking”, “War Driving, “Wireless Sniffing” and “Unauthorized Access to your environment” When not secured, your wireless network can be the highway through the airways with malicious intent.
Legacy Security Is Not Enough
Many companies, including those in the T&L sector have antiquated technologies mixed with newer solutions. Traditional security updates may only be available for some components but not older ones. The difficulty and diversity of deployed technologies and patching strategies, as well as the risk of applying those patches, varies enormously. Most security tools do not support the the diversity of assets that are likely deployed leaving gaps in observability and increases risk of a severe breach. While these solutions may offer a sense of security, the actual protection is likely less than desired, leaving you exposed to cyber attacks including ransomware attacks and loss of intellectual property and data.
Additionally, organizations have relied on cookie-cutter audits to review existing security systems and practices. While it’s important to regularly review your security standards, it’s vital that auditors understand the existing and emerging threats specific to organizations and industries and to apply best practices as well as compensating controls when a system is simply not compatible with a security control or practice.
Security practices should be specifically tailored not only to your industry, but to your organization.
About Cyber Insurance…
Cyber insurance is a common “add-on” to corporate policies and cybersecurity strategy in an attempt to mitigate the fallout and impact of a breach. However, the majority of cyber insurance policies do not protect against Cyber Ransomware attacks. As ransomware and other sophisticated attacks become increasingly common, its vital companies find solutions to protect against cyber attacks as after-the-fact insurance is less effective and costly.
Cyber Insurance companies have also tightened requirements in order to obtain that insurance, including evaluating the cybersecurity posture of an organization. From every angle it is cheaper, more effective, and a good investment to embrace and implement strong cybersecurity practices.
Incorrect Software Setup
Misconfiguration of the numerous software, operating systems and application versions leaves companies security posture weakened and vulnerable to attack. Common causes for misconfiguration are untrained personnel, poorly documented configuration changes and understaffed departments.
Infrequent Security Audits
Security auditing helps to protect critical data, identify security loopholes and potential threats. It will also help to detect high-risk practices and procedures and detect insider threats when routinely reviewed.
Only using threat detection (not hardening)
Implementing security measures in the form of OS / Application updates and security patches reduce the surface attack within the environment. Threat detection warns of malicious activity while hardening reduces security risks by eliminating potential system exploits.
Oteemo Can Help Defend Logistics and Trucking Companies Against Cyber Attacks
Oteemo’s Cybersecurity (Secure Architecture) offering is designed to mitigate impact by securing your existing architecture, assets, networks, and other devices and help prevent intrusions through tailored recommendations specifically for your organization and existing technology.
Oteemo’s approach to transportation and logistics security is derived from the U.S. Government’s Cyber Infrastructure and Security Agency (CISA) best practices and guidelines. CISA has issued implementation guidance for securing transportation Systems Sector Adapting this and our associates extensive experience in cybersecurity, at a high level Oteemo will:
- Characterize current cybersecurity posture and produces a broad spectrum roadmap and gap analysis
- Identify opportunities for enhancing existing cyber risk management programs that exist and how to complement those practices to achieve a highly effective cyber defense strategy
- Utilize industry standard tools, compliance standards, and methodologies specifically tailored to the T&L sector and your organization.
- Aggregate and synthesize your risk management and cybersecurity practices to key stakeholders to ensure transparency, knowledge transfer, and continuity
The Oteemo Path to Secure Architecture
1
Let’s see where you are
CISA RECOMMENDATION
Characterize your current cybersecurity posture.
Discover opportunities for improvement with our Comprehensive Risk Assessment. Our initial risk assessment will evaluate vital assets and provide a thorough overview of your existing security posture.
2
Your Environment Is In Good Hands
CISA RECOMMENDATION
Identify opportunities for enhancing existing cyber risk management programs.
We will collaborate with your team’s engineers and architects to design, improve, and implement a fortified environment.
3
Building Your Solution
CISA RECOMMENDATION
Find existing tools, standards, and guides to support Framework implementation.
We’ll create a comprehensive roadmap for implementation that outlines key milestones to achieve the desired end state. Day-to-day operations and continuous monitoring play a vital role in detecting compliance and risks in real-time; we can provide strategies to help mitigate current weaknesses and create a more secure environment.
4
Your Team Comes First
CISA RECOMMENDATION
Communicate their risk management issues to internal and external stakeholders.
As solutions are implemented and risk management issues arise all information will be relayed and shared with key stakeholders.
Offensive Security Services
We’ve developed a reputation for delivering high-quality, comprehensive services that meet the highest standards in the industry — and that means working with our clients to design solutions that meet their unique needs.
End-To-End Safety
Application Security
Oteemo’s in-depth offerings will help you secure your applications, employ DevSecOps, and ensure compliance.
Protected Infrastructure
Network Security
Prevent access to sensitive data and systems by locating attack paths, exploit chains, and vulnerabilities.
Secure Hosted Environments
Cloud Security
Uncover vulnerabilities, and deploy strategies to mitigate exploits in cloud based environments.
Protection Against
Ransomware Attacks
Oteemo has partnered with multiple organizations to review and enhance their cybersecurity posture in multiple sectors.
After Oteemo’s full review, the team will prescribe catered recommendations to meet your organization’s security needs.
Security Best Practices and Security Frameworks
With the risk assessment in hand, Oteemo will identify additional security measures that can be implemented to protect from and prevent against security threats. Best practices can be the baseline to augment additional regulations / guidelines your organization is required to adhere to. Depending on the security framework you are required to use, Oteemo has a wide range of experience and knowledge in deciphering and implementing security requirements.
Security You Can Trust
Oteemo has deep expertise in cybersecurity and securing architecture. From on-prem to cloud solutions, Oteemo has been trusted to diagnose and review security concerns in companies across the globe, including those requiring the highest DoD Impact levels.
Whether you’re looking to review and enhance your existing cybersecurity posture, or would like to migrate and grow into using cloud solutions, DevSecOps, or leverage a microservices architecture, Oteemo is your trusted partner on your security journey.
Success Stories
Oteemo deployed a secure, fully automated AKS cluster completely through gitops with versioned changes and approvals to a large healthcare company, demonstrating our ability to automate and secure cloud deployments, adhere to existing compliance requirements, and meet client’s needs.
Success Stories
Oteemo engineers engaged in cybersecurity work for Platform One in multiple innovative areas, including the Iron Bank, Big Bang, and CNAP (Cloud Native Access Point).
Success Stories
Collectively, Oteemo has experience architecting environments for compliance and security frameworks such as PCI and CMMC and always approaches engineering with a “security first” mindset.
Success Stories
Collectively we have defended against and mitigated active attacks and then developed forward-thinking strategies and automation to detect and protect corporate assets and data.
Success Stories
Developed highly secure multi-cloud and hybrid networks and solutions.
Begin Your Cybersecurity Posture Upgrade Today
Cyber Attacks are a constant threat, so the best way to protect yourself and your organization is through a comprehensive review of your cybersecurity. The experienced team at Oteemo is ready when you are.
Sources
https://www.freightwaves.com/news/minnesota-trucking-company-hit-in-2nd-ransomware-attack
https://www.ccjdigital.com/technology/article/15064368/cyberattacks-in-trucking-rise-during-2020
https://www.tsa.gov/news/press/releases/2022/07/21/tsa-revises-and-reissues-cybersecurity-requirements-pipeline-owners
https://www.cisa.gov/stopransomware/resources
https://www.trendmicro.com/vinfo/us/security/news/internet-of-things/out-on-a-highway-run-threats-and-risks-on-its-and-smart-vehicles
https://www.cisa.gov/uscert/ncas/tips/ST05-003
https://www.forbes.com/sites/thomasbrewster/2016/03/09/remote-control-truck-hacker-threat/?sh=22e21f113395