Traditionally, a greater emphasis on an application’s performance is attributed to its scalability, user experience and efficiency. Out of the list of other critical factors that define the application’s success, ‘security’ remains at the very bottom. Combined with this, a siloed model that classifies every phase of an application workflow to be handled in stages, offers little collaboration and lack of ownership to tackle inherent vulnerabilities. Unsurprisingly, such frameworks remain widely exploited by cyber attackers, where Gartner predicts that through 2025, 99% of cloud security failures will be the customer’s fault.
In contrast to a traditional approach of building software, a DevOps model breaks operation silos to form an efficient framework of multi-team collaboration and continuous automation. As an evolution to DevOps’ capabilities, DevSecOps further enables a continuous testing framework with equal emphasis on security as with operational efficiency, innovation and agility. Leading to a shift-left for security approach, DevSecOps integrates security practices across all phases of a workflow – thereby identifying vulnerabilities and mitigating threats across all stages at the same pace as updated codes are pushed to the pipeline.
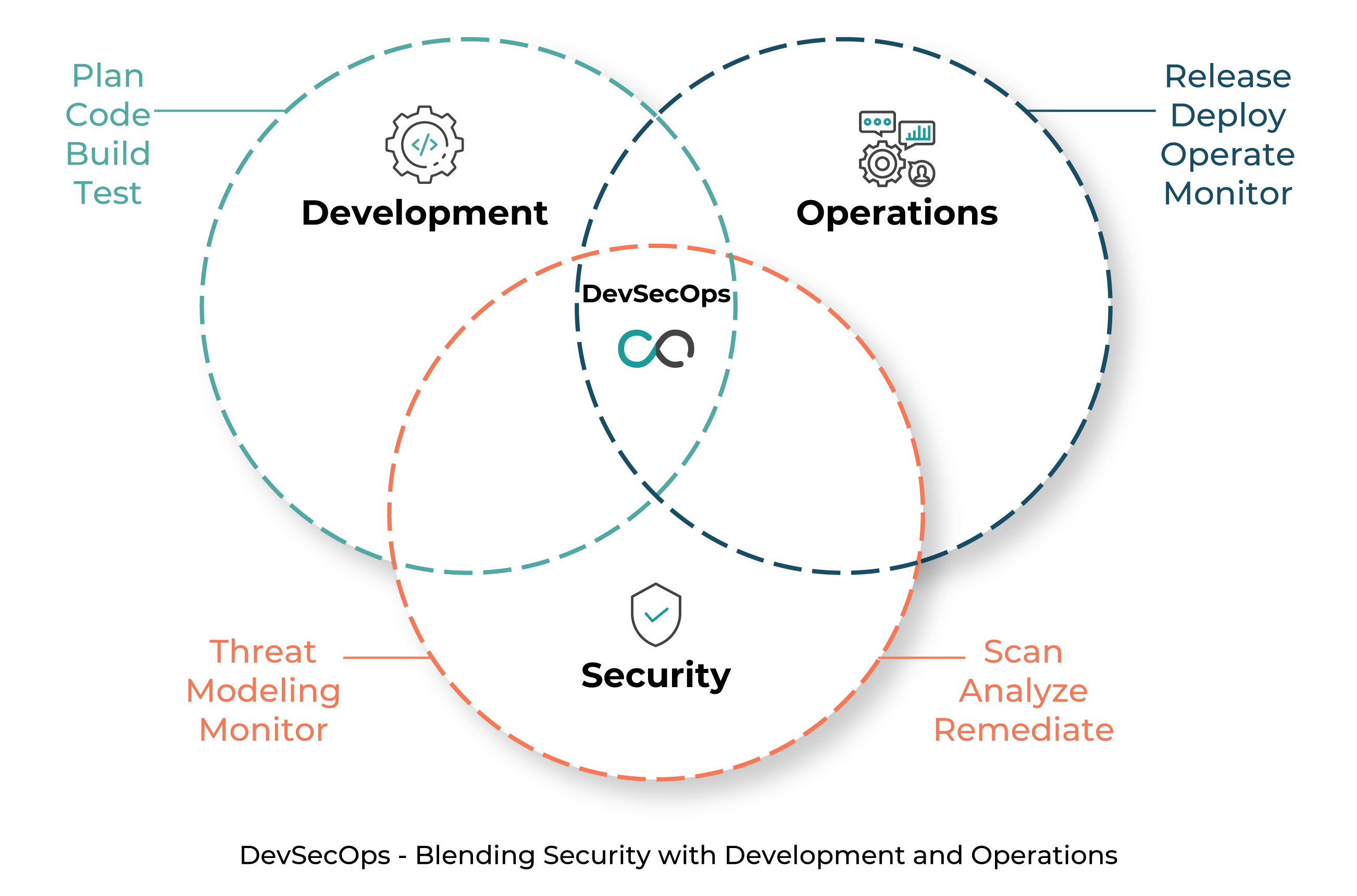
With DevSecOps, security is no longer an afterthought. The following sections highlight the best practices and benefits of embracing DevSecOps, emphasizing the importance of robust security in application development.
Benefits of Integrating Security in Modern Workflows
DevSecOps allows software teams to integrate security practices inside out, strengthening the overall security posture of an application’s lifecycle. While use cases differ for different organizations, here are some common benefits of embracing a DevSecOps model:
Increased Agility
Traditional development approaches relied on a siloed team model that introduced security at the end of the development cycle. As a result, tracking and remediating vulnerabilities most often reiterated the build phase – thereby resulting in an inefficient model that caused security to be treated as a bottleneck rather than an efficiency-enabler.
Contrary to a traditional model, DevSecOps enables organizations to develop a secure codebase quickly by applying security controls through each stage of development. The philosophy relies on flexible collaboration between code development, release management, and security administration to ensure every stakeholder contributes to application security. Additionally, by enforcing automated testing to ensure security threats are caught and remedied sooner, DevSecOps enables organizations to not only retain but enhance overall agility of an application workflow.
Enhances the Organization’s Security Posture
The fundamental principle of DevOps and DevSecOps is to enforce automation. By focusing on the automation of security tools and processes, DevSecOps enables a seamless continuous testing mechanism throughout the application’s lifecycle. A comprehensive automation is also enforced by automating proof of controls and event logging that help in reducing the resolution time of security incidents. As an outcome, security teams shift their focus on defining strategic security practices (proactive) rather than identifying gaps (reactive). Besides these, DevSecOps reduces governance & compliance costs, ensuring the organization is always ready for audits and follows the standard regulatory guidelines.
Enforce Governance (Policy & Compliance Framework)
An organization’s security posture is also derived by identifying its compliance to governance standards. Such standards include – HIPAA, GDPR, PCI-DSS, and similar – which outline regulatory guidelines to secure a tech stack and sensitive user data. To enforce such mandatory compliances, DevSecOps implements the automation of security audits and policy controls which scan an entire stack to report on the health of each component. Automated security tools also enable automated logging and infra monitoring as key processes to support advanced compliance reporting. These approaches are instrumental in not only ensuring compliance with security policies but also ensure quick mitigations in case of non-compliance. Furthermore, with enhanced code visibility and traceability on account of continuous scanning, auditing phases of the development life cycle is smoothened further.
Higher Code Quality
A key outcome of adopting DevSecOps is the practice of an efficient threat modelling mechanism, which assesses multiple scenarios to help gain insights into how an attacker can access and exploit the system. To do so, different teams collaborate and peer-review each other’s codes to identify flaws. In addition to this, DevSecOps encourages the use of various tools for automated and continuous code scanning to trace vulnerabilities. This makes it easy to diagnose potential security weaknesses, resulting in a finer code quality before its pushed to production.
Cost Savings
Automating security checks leads to a faster detection, identification and remediation of security threats. By proactively mitigating security threats and malicious actors before release, organizations spend up to 3x less to secure their software. Proactive prevention also eliminates bottlenecks associated with siloed security practices at the end of the development cycle, reducing the costs associated with breaking code repeatedly to fix vulnerabilities. DevSecOps’ faster deployment speeds also ensure higher profitability since markets favour agile, secure software products.
Embracing DevSecOps
To blend security with high-velocity application development, organizations must enforce a culture of collaboration and authority among siloed teams who traditionally focus on only one aspect of an SDLC. This section delves into the practices and tools that help consolidate security into an application lifecycle without compromising on efficiency and resilience.
Implementing DevSecOps – Best Practices
The benefits of embracing a DevSecOps model are a dime a dozen. With benefits, though, organizations must be equally wary of the challenges and the critical factors that decide the success of its implementation. Following are some of the best practices that complement agile applications with a robust security framework:
Security at the centre of a lifecycle
Enabling a DevSecOps culture starts with a shift-left for security approach. Though the name says otherwise, the approach integrates security as the central pillar of a CI/CD pipeline. The approach introduces automated security mitigation that requires minimal human intervention for seamless development, operations, and code quality. An essential aspect of doing so requires refactoring and restructuring the CI/CD pipelines, source control repositories, and container registries for automated orchestration and auditing vulnerabilities.
Embrace Microservices and Infrastructure-as-Code
Breaking monolithic software into loosely-coupled microservice-based applications allows for easier logging and monitoring of application flaws. As it is both easier and cheaper to fix vulnerabilities in small, containerized services, such a framework enables high-scalability, enhanced agility and robust security. Additionally, packaging infra services, policies and security as code allow for easier bug traceability, security audits, and threat mitigation.
Brainstorming teams on the importance of Security
The adoption of DevSecOps often starts with a change in organization-wide mindset that understands the importance of security. It is essential that every stakeholder understands security practices and takes corrective actions to achieve comprehensive compliance. This also requires a planned approach to imparting training, conduct mock drills, and creating playbooks that clearly outlines everyone’s role and shared responsibility in keeping the system safe.
Embracing Application Security Mechanisms
The DevSecOps methodology relies on several testing mechanisms for application security. Such mechanisms help identify vulnerabilities across different stages of an SDLC, allowing for end-to-end threat management. These include:
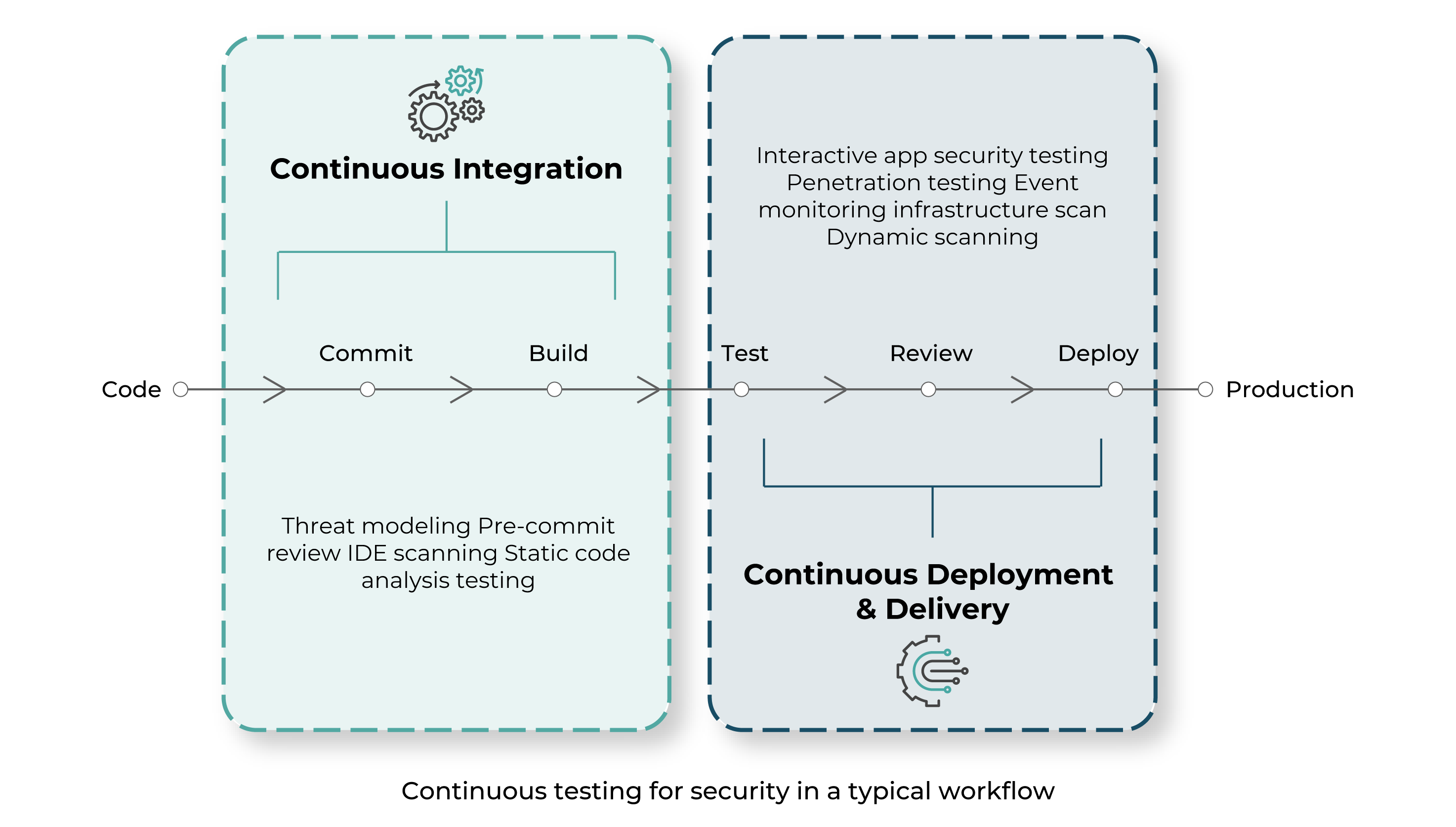
Static Application Security Testing (SAST)
Also known as the White-Box approach, this mechanism inspects vulnerabilities within a pre-compiled source code. As one of the most commonly used methods to diagnose issues within source code, byte code and libraries during the pre-deployment phases, SAST identifies vulnerabilities, such as syntax errors and invalid references.
Dynamic Application Security Testing (DAST)
Contrary to SAST, this mechanism is referred as Black-Box testing that spots runtime security vulnerabilities and is used to inspect issues with query strings, cookie handling, scripts, and data injection.
Interactive Application Security Testing (IAST)
IAST involves running an agent inside an application to find vulnerabilities within both pre and post-compiled application code. Considered as the most preferable approach to test APIs, IAST is also widely popular in inspecting data flow, configuration files, component-level interaction, libraries as well as source codes.
Runtime Application Self Protection (RASP)
RASP represents a proactive mechanism to track and analyze user behaviour and traffic load in production workloads. The mechanism allows security teams to detect runtime vulnerabilities and defer potential attacks.
Conclusion
A half hearted approach to tackling vulnerabilities is equivalent to an improperly configured security framework. The fundamental reason for an underperforming security framework is that it is rarely considered as a success factor of application delivery. DevSecOps solves this by administering continuous security across all layers and stages of an SDLC. The outcome is an efficient workflow that is agile and secure. As added advantages, the model also enhances wider collaboration, reduced operational overheads, and automated policy compliance.
Per GitLab’s 2020 DevSecOps survey, more than 65% of surveyed organizations accepted to be already using a DevSecOps model. Out of which, 83% have confirmed that they are already benefiting from high-velocity, efficient releases – alongside the aspect that security is no longer compromised.









0 Comments