In light of the drastic increase in cyber attacks, Oteemo decided to look into the Trucking and Logistics spaces and because it has such a large footprint, it also has great potential to incur some very costly incidents. Fascinated by all the areas for a potential breach, I wanted to be part of the creation of an Oteemo service offering that could be invaluable to the trucking industry.
With decades of knowledge and experience in Information security, I learned about an emerging threat to the cybersecurity world, and a new target malicious attackers have set their sights on the trucking and logistics industry. What I discovered were familiar attacks targeting an unprepared industry ripe for exploitation. I and a few other members of Oteemo led a team to create a service offering to combat the threat and assist the trucking industry in defending themselves.
The Statistics Tell A Frightening Story
I began poring through websites, whitepapers, industry-compiled statistics, and security analysis reports and what I found truly amazed me:
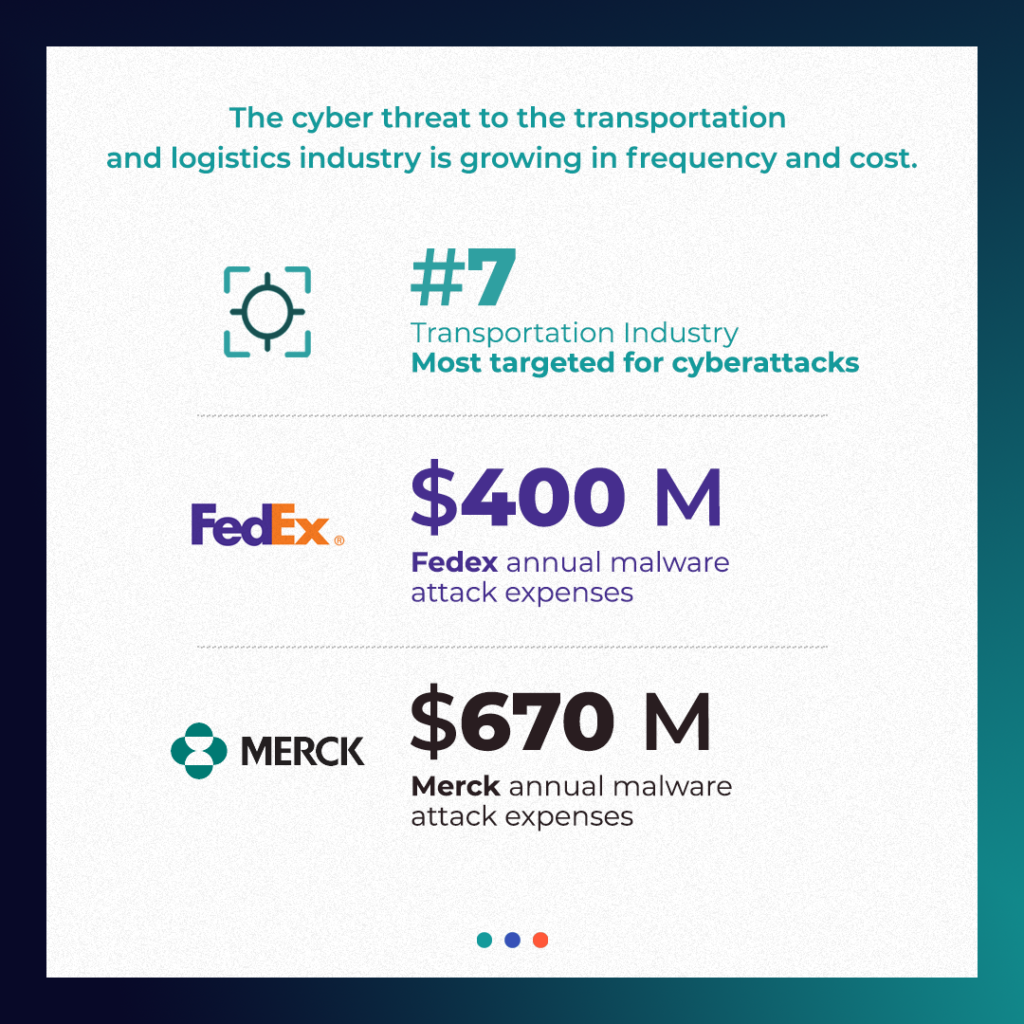
- An IBM study showed that 4% of all cyberattacks were aimed at the transportation industry, making it the 7th most targeted industry in the past year. Between June of 2020 and June of 2021, the transportation industry witnessed a 186% increase in ransomware attacks.
- FedEx says its expenses tied to malware attack was $400 million over the past year.
- Merck put costs at $670 million in 2017. The sophistication of the attackers and their attacks has grown significantly since then and without a strong security posture, remediation costs will continue to rise.
As the attacks began they were similar to what I’ve seen in other industries, but as the attackers became more familiar with the industry, they started targeting riskier areas including regulations, specialized trucking applications, and the different types of networks associated with transportation from vehicle bus networks – Internet of Vehicles (IoV) distributed networks. Once specific trucking industry ingredients are introduced to the equation, additional steps must be taken to enhance your company’s security posture.
In 2021, trucks moved 10.23 billion tons of freight totalling over 827 billion dollars which is up 7.2% from 2019. To make this happen, there are hundreds of different applications that drivers use to help with truck stop locations, weigh stations, fueling stops, route planning, rest areas and food along their routes. With all the different software applications, this opens the door to a variety of vulnerabilities and access points an attacker could use as a welcome mat into your environment. If any of the software/application versioning isn’t kept current or the device they are installed on isn’t properly configured, you could be handing over the keys to your kingdom.
Cybersecurity and Infrastructure Security Agency (CISA), categorizes the transportation industry as a critical infrastructure industry. In the 2022 IBM Cost of a Data Breach report, “Ransomware attacks accounted for 12% of critical infrastructure breaches, while destructive attacks were behind 16% of critical infrastructure breaches, for a combined 28%. Another 17% of breaches in these industries were supply chain attacks where a third-party business partner was the attack vector. Meanwhile, breaches caused by human error or IT failures accounted for 22% and 25%, respectively. The remaining 8% of critical infrastructure breaches were other malicious attacks.”
BYoD – The good, the bad and the ugly!
The concept of Bring Your Own Device (BYoD) has skyrocketed in recent years. Convenience, productivity, lack of company resources and employee satisfaction are some of the largest factors. On the flip side of convenience are the mounting risks. Improper device configuration or patch/update status can be very daunting given the vast number of device models, versions, and types. Lost or stolen devices, malware, and connecting to and doing business on an unsecured wireless network are all high risks where your company’s future is concerned.
Cybersecurity Best Practices For The Logistics Industry
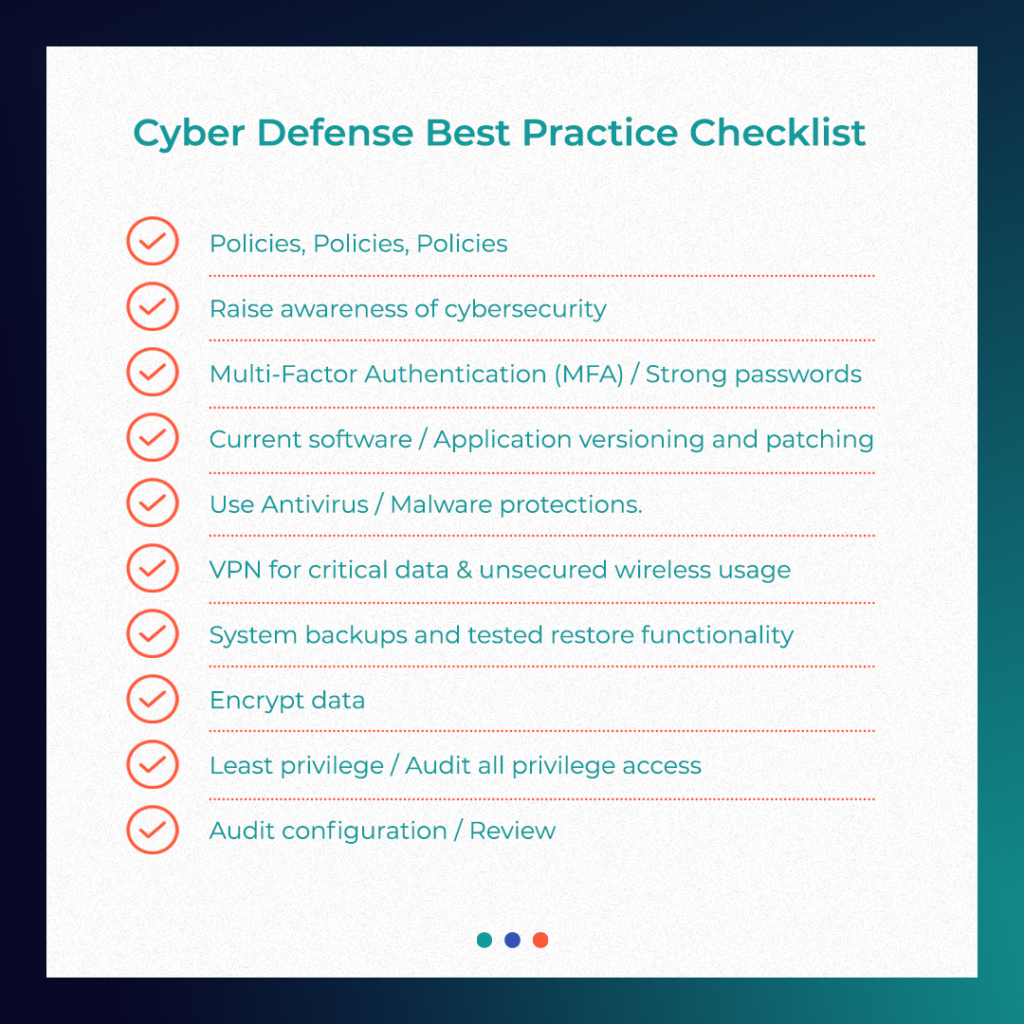
Whether an attack grants access to the payload or the company is hit with a ransomware attack, some of the risks can be averted by implementing cybersecurity best practices. Baseline security steps can be a much-overlooked first defense and they are usually pretty standard across the board. Here is a great start on Cyber defense best practices that Oteemo can elaborate on as to how they could apply and reduce the risks your environment currently faces.
Oteemo Can Help!
Evaluating the cyber posture of your company may seem like a “nice to have” or outside the expertise of current IT staff or the financial budget of small to mid-sized trucking companies. The unfortunate alternative is leaving your company open to massive risk. The good news is, there are steps you can take to mitigate the risks the trucking industry now faces. Oteemo has the width and breadth of knowledge and experience to evaluate your environment and make recommendations that will enhance your security posture. We’ve been trusted by companies and organizations from a variety of industries including those working with the U.S. Government and the Department of Defense. Simply put – Oteemo knows how to help organizations defend themselves from malicious attacks, contact our team today.
FAQs Related to Logistic Security
What examples are there of logistic communication vulnerabilities?
Logistics vulnerabilities have been documented in a number of attacks. These attacks range from simple phishing attacks to more complex attacks such as “Piggybacking”, “War Driving”, and “Wireless Sniffing.”
While these attacks range in complexity, any unauthorized access can lead to extensive vulnerabilities.
How large of a threat are the communication vulnerabilities?
Vulnerabilities in any area are a threat to the entire cyber security of an organization. Every threat must be taken seriously as even minor exploits can lead to major issues.
What are logistic companies doing about the system communication vulnerabilities?
Many logistics companies have taken various steps to harden and mitigate any vulnerabilities in their systems. This ranges from cyber security training for all employees to a complete cyber security posture review. It’s vital to understand how your organization can stand up to cyber security threats and understand the gaps that could be exploited so you can properly defend against attacks.








0 Comments